While that’s behind us, last week’s controlled reveal of the Spectre and Meltdown security flaws, which were originally thought to have affected only Intel processors, have expanded in reach to even Apple’s A-series CPUs. Today, Apple released a major update with a fix for all supported iOS devices affected by the Spectre and Meltdown vulnerabilities.
Apple Releases Critical iOS 11.2.2 Update with Fixes for Spectre and Meltdown Vulnerabilities
While iOS updates are known for the usual bug fixes, performance and feature improvements, this release is one you probably want to do your utmost best to download as soon as possible. Spectre and Meltdown are severe vulnerabilities that affect how the brains of your iOS device execute code. This hole opens up your device making it possible for hackers to access sensitive information such as passwords, pictures, and banking information.
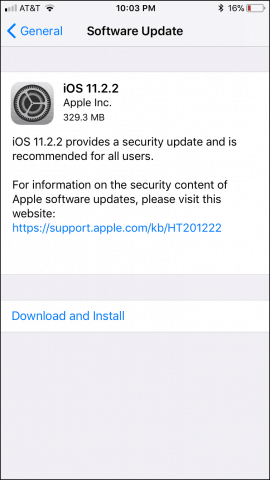
The iOS 11.2.2 update is just 64 MBs and is available for devices such as the iPhone 5s and later, iPad Air and later, and iPod touch 6th generation. Users can download the update by connecting to a wireless network, launch Settings > General > Software Update then tap Download and install. The update specifically targets Spectre and Meltdown, so, no additional surprises there. Apple’s other devices such as Apple Watch and Apple TV are not affected by this flaw. If you use a Mac, there is also a Spectre update for your system. Usually, at this point in the article, we ask whether you should upgrade now or wait it out a bit. But this time around, we recommend you jump on this update right away. You might want to make a quick backup just in case something bad happens. Last month, while attempting to install 11.2.1, I experienced some issues on my iPhone 6s. Description: iOS 11.2.2 includes security improvements to Safari and WebKit to mitigate the effects of Spectre (CVE-2017-5753 and CVE-2017-5715). Source The update failed a couple times during installation but automatically recovered. It has been revealed that Apple started mitigating the Meltdown attack in 11.2. This might have been the contributing factor to the long time it took to install – just speculating of course. Although Apple and other software firms and Internet companies were aware of the problem as far back as summer 2016, it was eventually leaked out. There is a possibility that hackers might be trying to cook up something quickly to cause damage, especially for high profile platforms such as iOS and Windows. So, grab this update as soon as you can and report back in the comments your experience with the update. It is an issue that has existed for 20 years. At the time I write this, there are no known imminent threats out in the wild. It’s something that consumer should be aware of, like all exploits, and it’s important to make sure your devices are updated. However, this will not slow down your modern phone Mac or PC. However, there have been issues with older AMD systems but Microsoft has since pulled that buggy patch. For more details and links to detailed explanations on this, check out my post in our Windows 10 Forums: https://windows10.help/topic/826-calm-down-the-meltdownspectre-issue-isnt-the-end/?tab=comments#comment-2851 So far — I’ve not seen any data on this for mobile devices. However, here’s what Microsoft is saying about its Desktop and Server code: https://cloudblogs.microsoft.com/microsoftsecure/2018/01/09/understanding-the-performance-impact-of-spectre-and-meltdown-mitigations-on-windows-systems/ Below is what the Executive VP of Windows and Devices is saying. Not good for older devices…. Here is the summary of what we have found so far: With Windows 10 on newer silicon (2016-era PCs with Skylake, Kabylake or newer CPU), benchmarks show single-digit slowdowns, but we don’t expect most users to notice a change because these percentages are reflected in milliseconds. With Windows 10 on older silicon (2015-era PCs with Haswell or older CPU), some benchmarks show more significant slowdowns, and we expect that some users will notice a decrease in system performance. With Windows 8 and Windows 7 on older silicon (2015-era PCs with Haswell or older CPU), we expect most users to notice a decrease in system performance. Windows Server on any silicon, especially in any IO-intensive application, shows a more significant performance impact when you enable the mitigations to isolate untrusted code within a Windows Server instance. This is why you want to be careful to evaluate the risk of untrusted code for each Windows Server instance, and balance the security versus performance tradeoff for your environment. For context, on newer CPUs such as on Skylake and beyond, Intel has refined the instructions used to disable branch speculation to be more specific to indirect branches, reducing the overall performance penalty of the Spectre mitigation. Older versions of Windows have a larger performance impact because Windows 7 and Windows 8 have more user-kernel transitions because of legacy design decisions, such as all font rendering taking place in the kernel. We will publish data on benchmark performance in the weeks ahead. Comment Name * Email *
Δ Save my name and email and send me emails as new comments are made to this post.
![]()